2022腾讯游戏安全PC初赛
初赛题
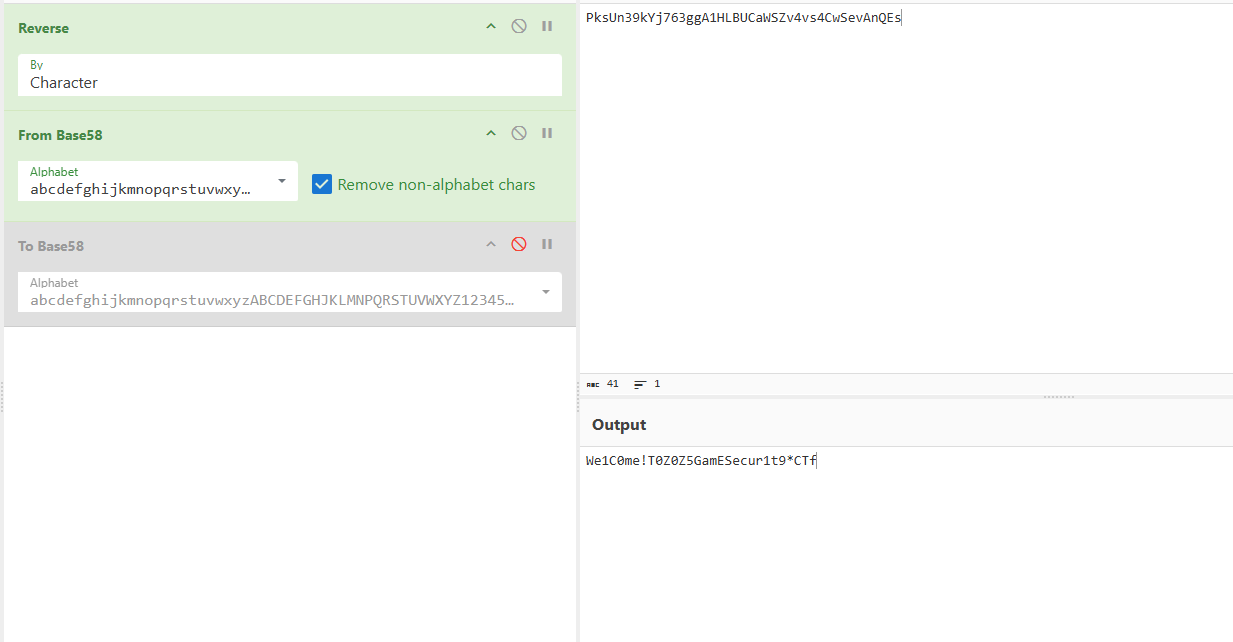
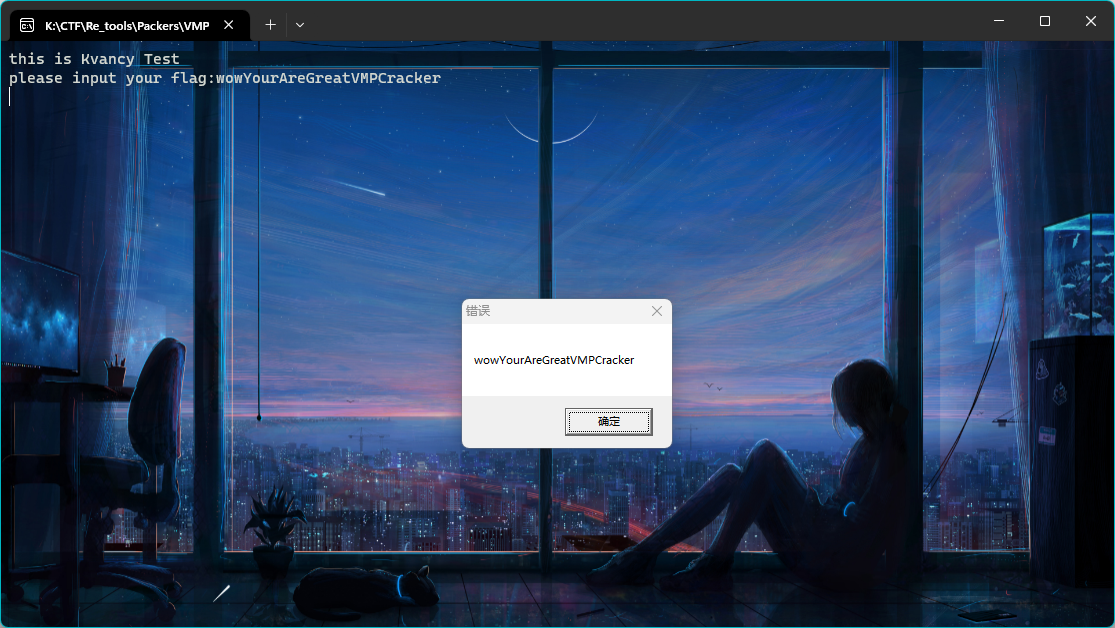
这里有一个画了flag的小程序,可好像出了点问题,flag丢失了,需要把它找回来。
题目:

找回flag样例:

要求
1、不得直接patch系统组件实现绘制(如:直接编写D3D代码绘制flag),只能对题目自身代码进行修改或调用。
2、找回的flag需要和预期图案(包括颜色)一致,如果绘制结果存在偏差会扣除一定分数。
3、赛后需要提交找回flag的截图和解题代码或文档进行评分。
DIE查壳,PE64位无壳,先IDA静态分析看一下
定位到这个函数
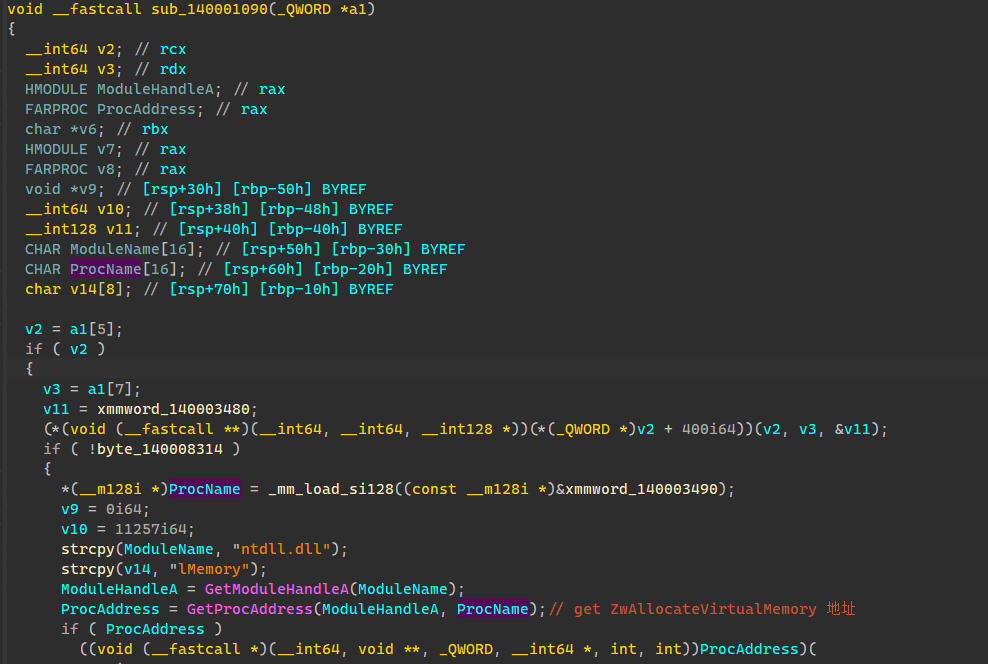
该函数先是加载了ntdll系统模块,再进行拼接字符串获取该模块ZwAllocateVirtualMemory函数地址
1 | NTSTATUS ZwAllocateVirtualMemory( |
接着往下看
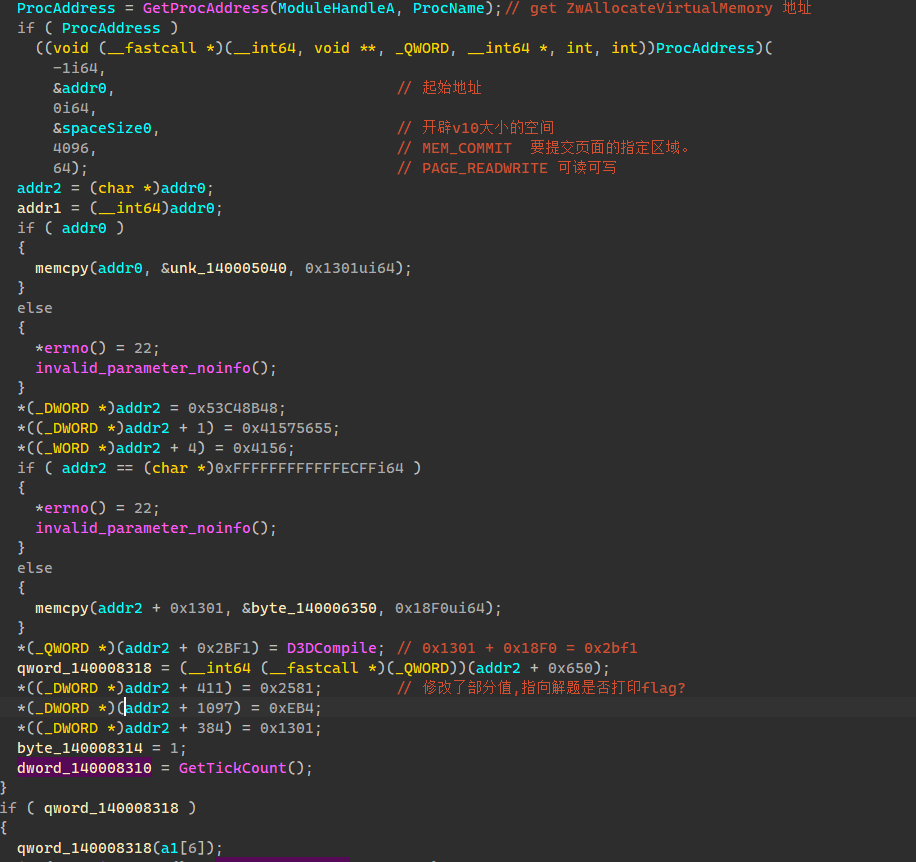
先是利用ZwAllocateVirtualMemory开辟了一块0x2BF9可读可写的地址空间,随后在该地址空间填入数据,最后再对地址空间部分数据进行了修改,qword_140008318可能是一个函数地址,在最后调用了这个函数,然后等待一段时间就释放了这个地址空间,所以绘画逻辑应该是在这个函数里,绘画完之后展现一段时间后消失和运行效果相同
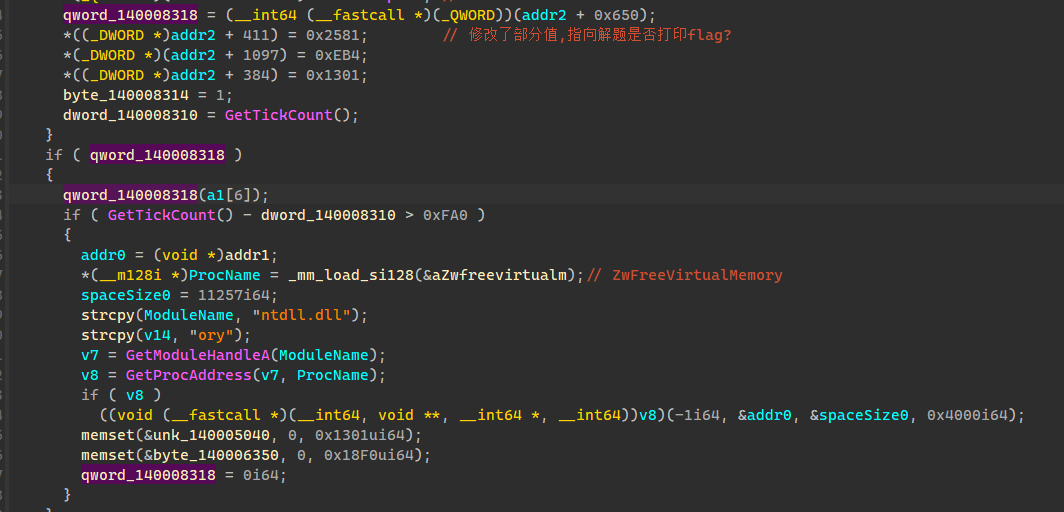
所以主要逻辑应该是在qword_140008318函数里,x64dbg调试看一下,定位到qword_140008318赋值语句,00000001400011FE地址处下断点
1 | 00000001400011FE | 48:8905 13710000 | mov qword ptr ds:[140008318],rax | |
进入rax发现确实是一个函数地址
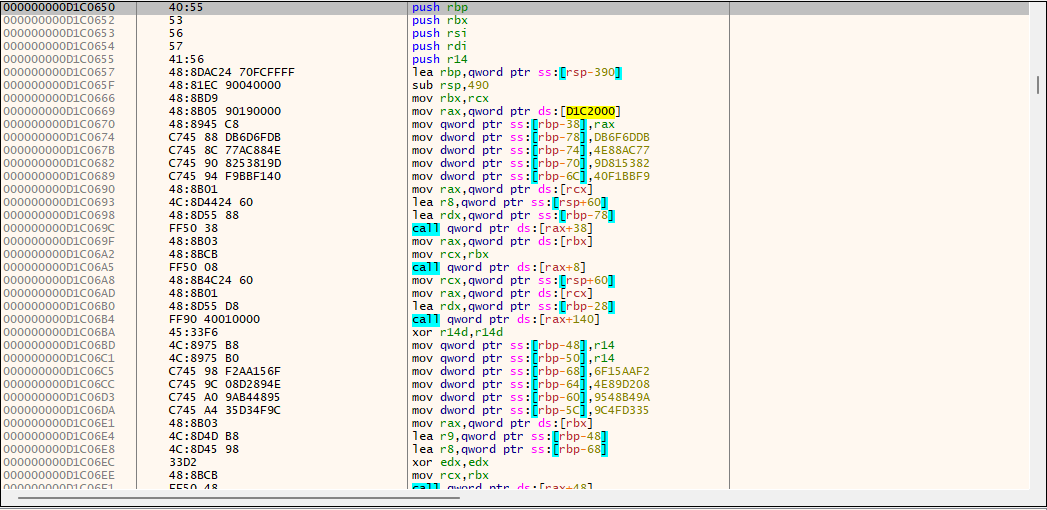
再看一下修改部分的数据代表到底什么意思
1 | 00000001400011FE | 48:8905 13710000 | mov qword ptr ds:[140008318],rax | |
分别定位到rbx对应的偏移处找不同
第一处 mov dword ptr ds:[rbx+66C],2581
1 | 000000000D1A0666 | 48:8BD9 | mov rbx,rcx | |
第二处 mov dword ptr ds:[rbx+449],EB4
1 | 000000000D1A0442 | 4C:8B65 70 | mov r12,qword ptr ss:[rbp+70] | |
第三处 mov dword ptr ds:[rbx+600],1301
1 | 000000000D1A05FD | 48:81FE 8F050000 | cmp rsi,58F | |
第一处和第二处nop掉直接程序出现异常
第三处nop掉发现会对绘画效果产生影响,这里少了五个方块,
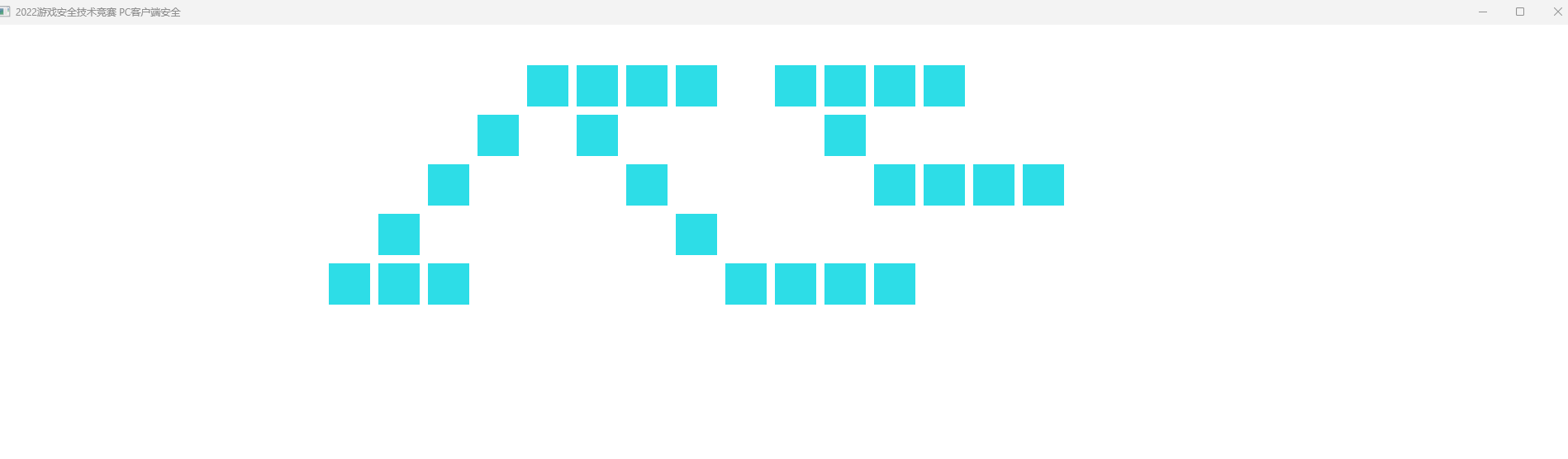
所以[rbx+600]处附近会可能有绘画逻辑,运行到附近看看
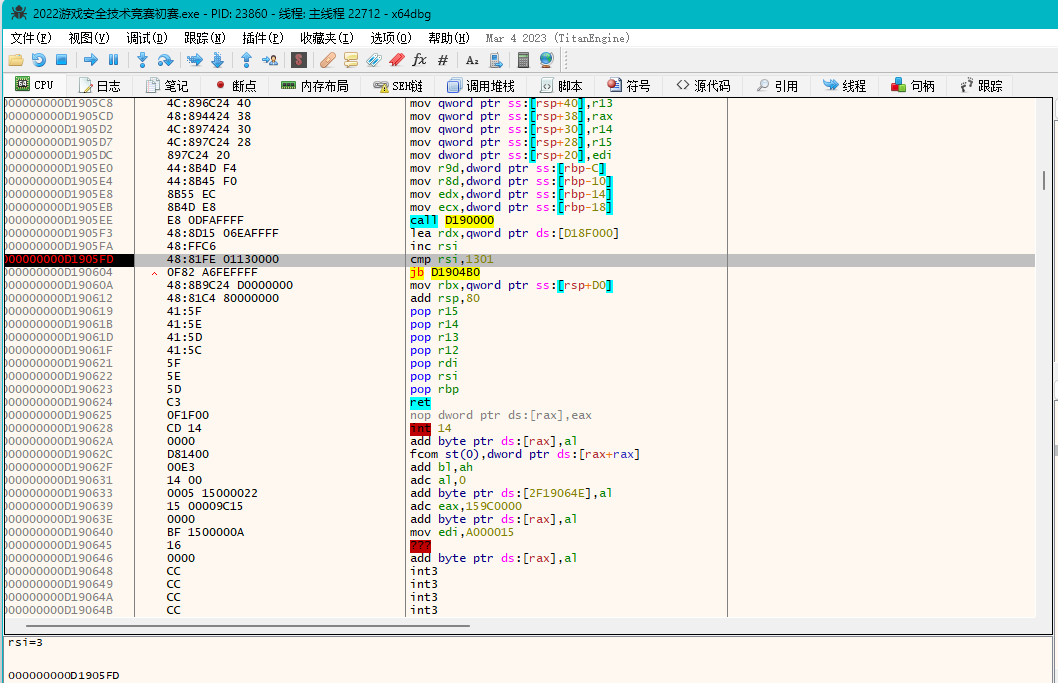
分析这个函数,这里的rsi应该是一个数组的索引值,通过数组的值是否等于7进行判断,应该是将有效值和无效值进行区分,然后遍历了整个数组,进行了多次循环操作
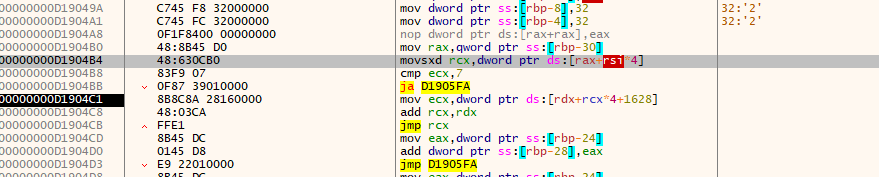
那有效值在哪呢,我们主要找的绘画的浮点数位置保存在哪?D3D开发的经验不多,我就从一个个可能的函数的参数入手
看看是否能直接通过传参获取位置数组,这个函数里只有一个函数D190000
运行到该函数,观察函数传参窗口
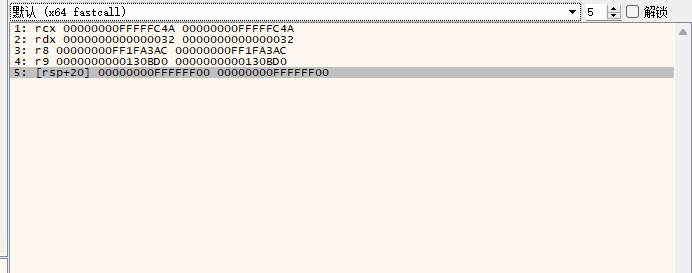
显然没有这么容易,那还有可能在这个函数的母函数或者子函数的函数里
通过堆栈回溯找到母函数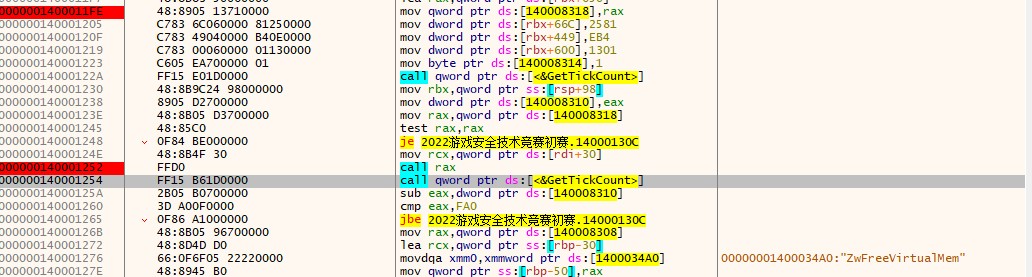
这个rax是之前分析过了的函数地址,所以这个函数就是位置数组的出处了
进入分析
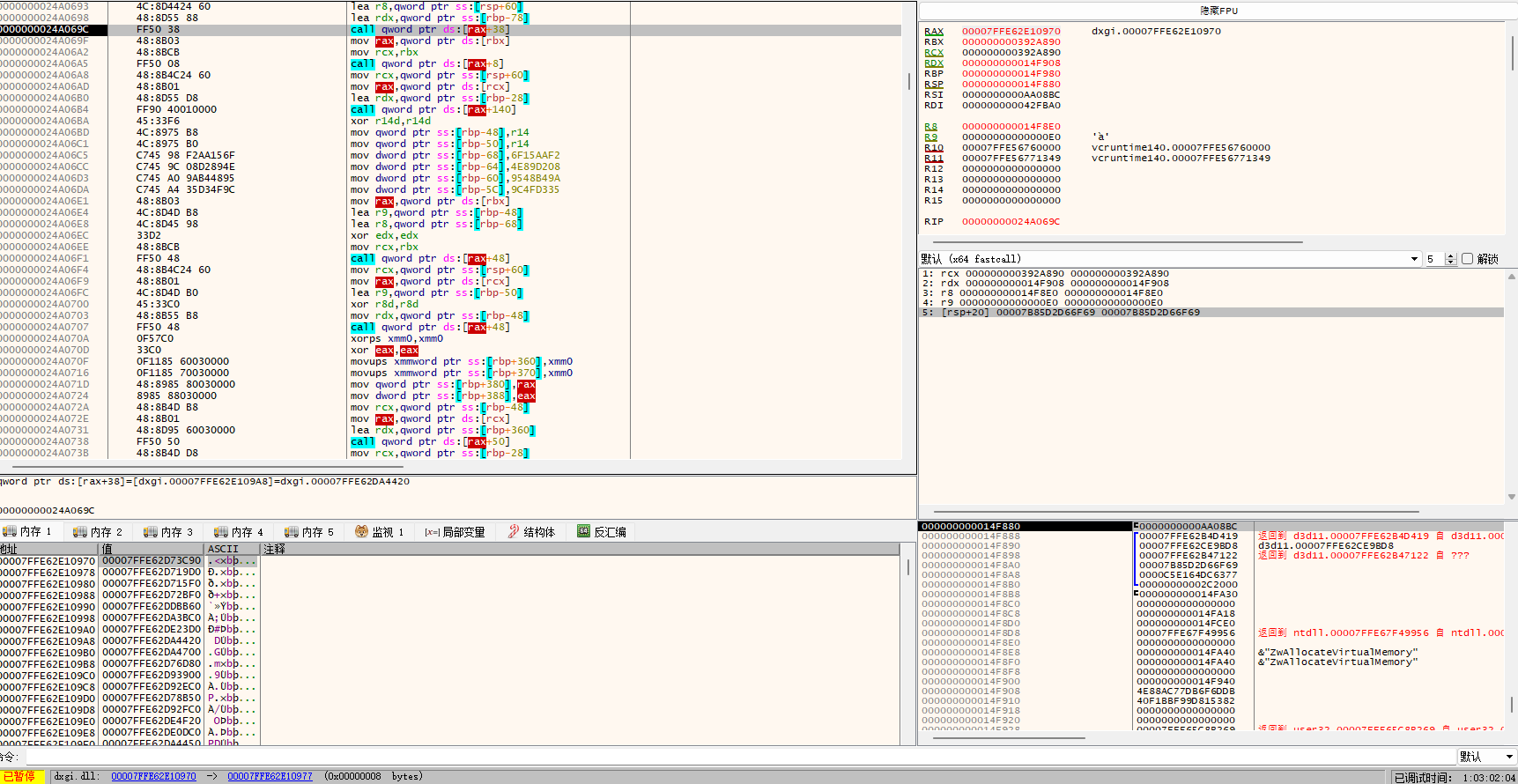
调用了一堆系统函数,并没有明显传参,也没有浮点数处理的汇编指令,这些略过分析,继续看
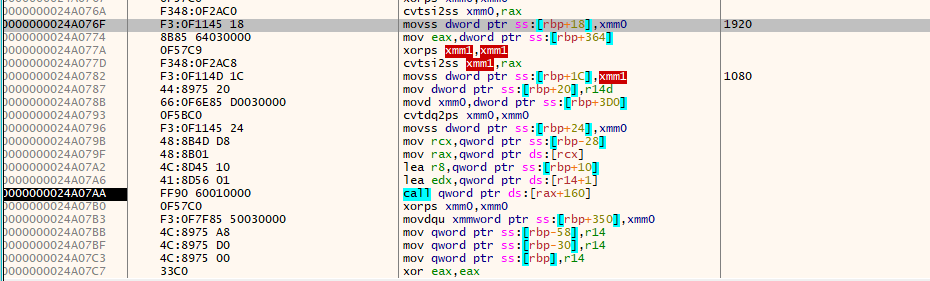
这里传入了两个浮点数,一个1920,一个1080,分辨率大小? 应该是绘画的初始化操作,继续分析找浮点数数组
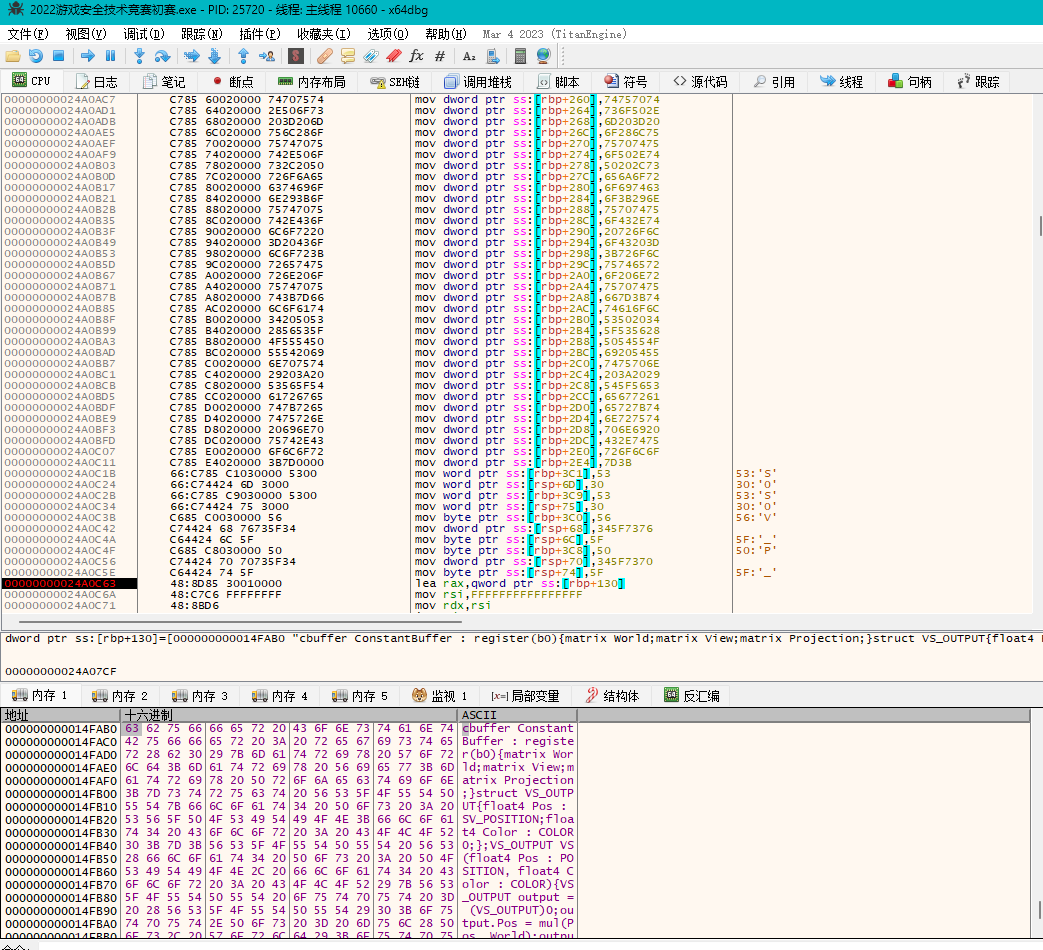
这里有个缓冲区,存储了HLSL语言编写的一段顶点着色器和像素着色器的代码,进行图形渲染步骤,然后再调用了一些D3D函数
1 | // 定义常量缓冲区 |
下面还有一个
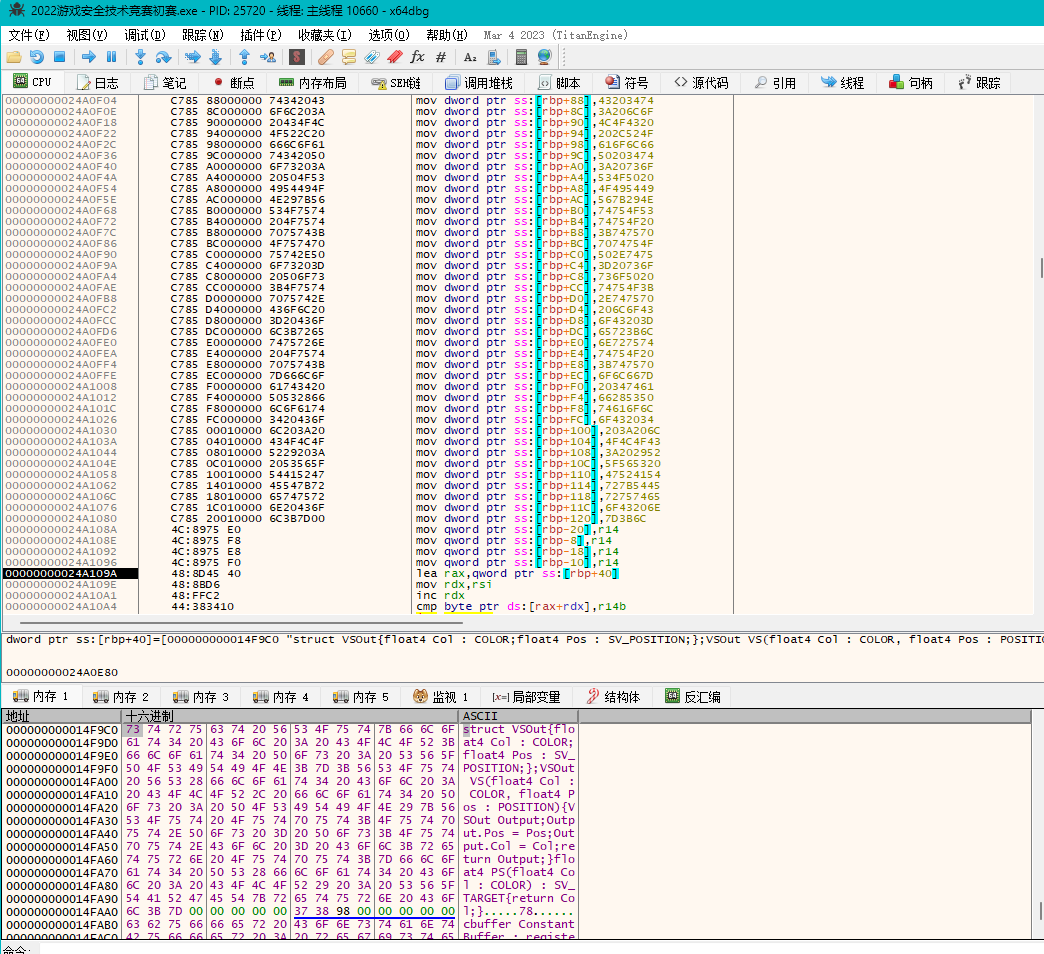
1 | // 定义顶点着色器的输出结构体 |
两个不同的着色器设计,是否对应了一个flag图形和原始图形两种图形不同的着色器呢?
但是最关键的位置数组我们还没找到,接着往下分析吧
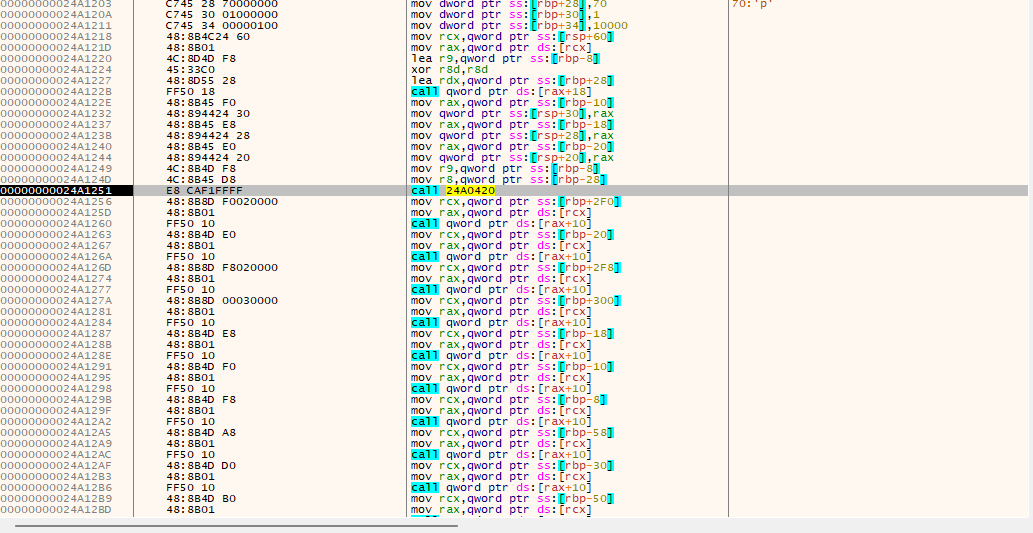
这个函数内部还有一个用户层函数,进入分析
发现这个函数内部就是刚刚回溯开始的函数,那就直接进入该函数的子函数分析
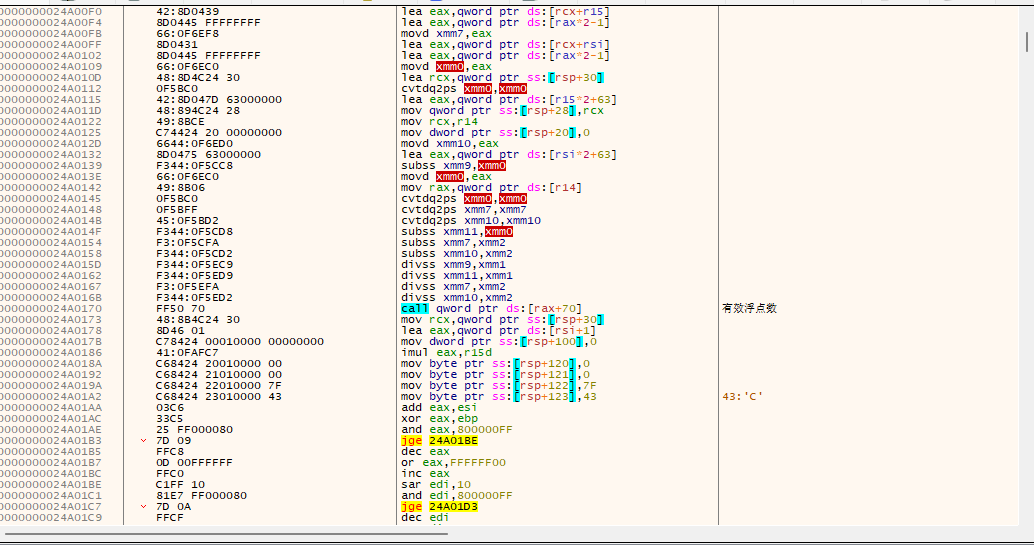
一堆浮点数处理的汇编指令,好像还进行了加密解密操作,所以这里应该就是浮点数数组的出处了吧
跳过这些计算浮点数的指令,直接找到赋值语句并定位位置数组的首地址
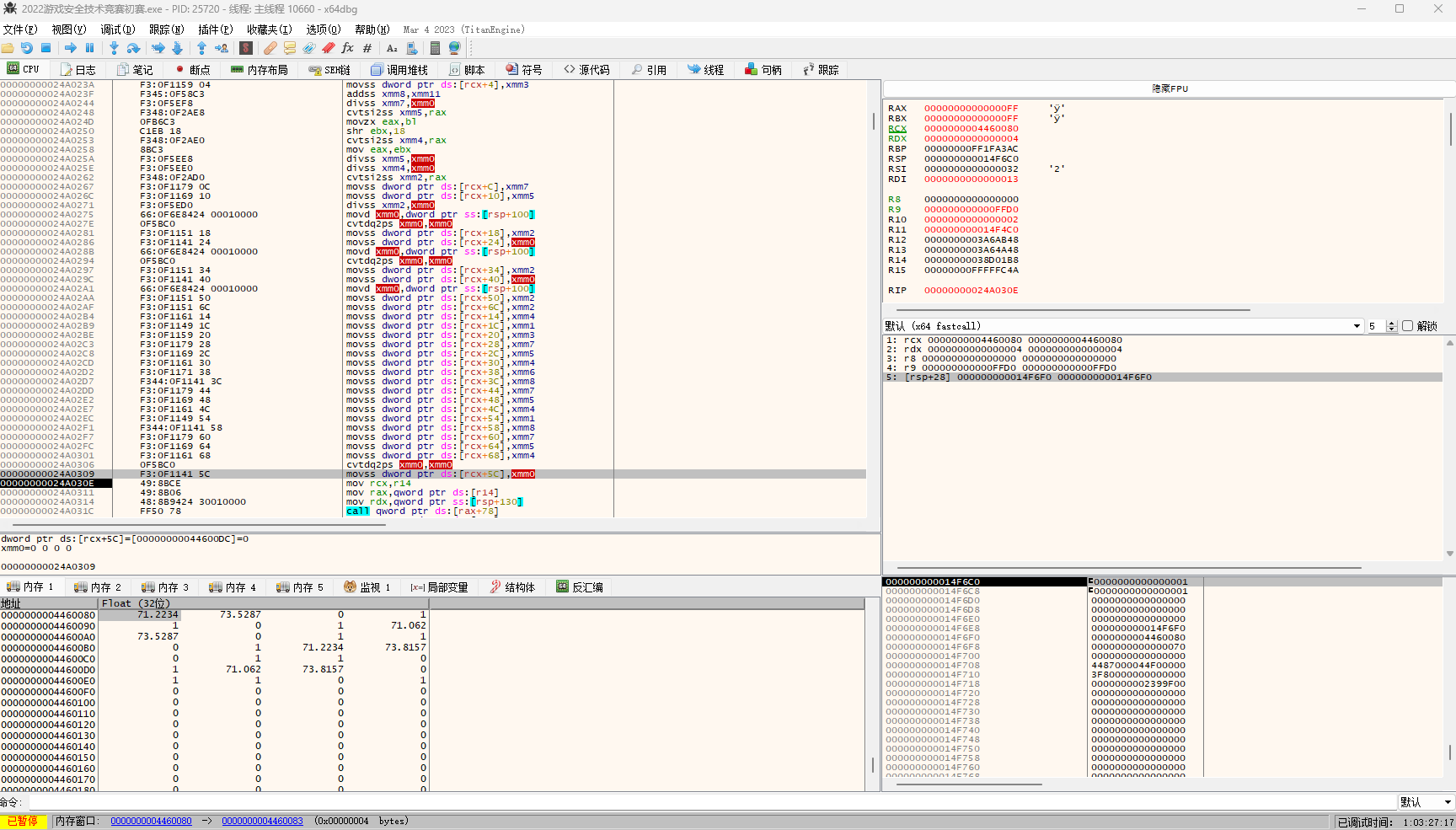
这里分析发现,rcx即为数组首地址,继续分析,后面就是继续调用D3D函数,但是我并没有发现数组怎么传进去的,只是找到可能的位置数组,这个函数运行到返回只提供了0x70大小的浮点数数组,但是我们在之前分析过了,这个函数会循环运行,循环运行完后导出这些浮点数.得到1340个浮点数,到这里我有点怀疑这个数组的真实性了,不应该有这么长的数据的,总共方块数是31+11=42个,点数就是42*4=168个点,就算是三维坐标也不超过这么多数据,但是我还是在python进行了一个绘制,这里是python绘制代码
1 | import struct |
运行结果如图:
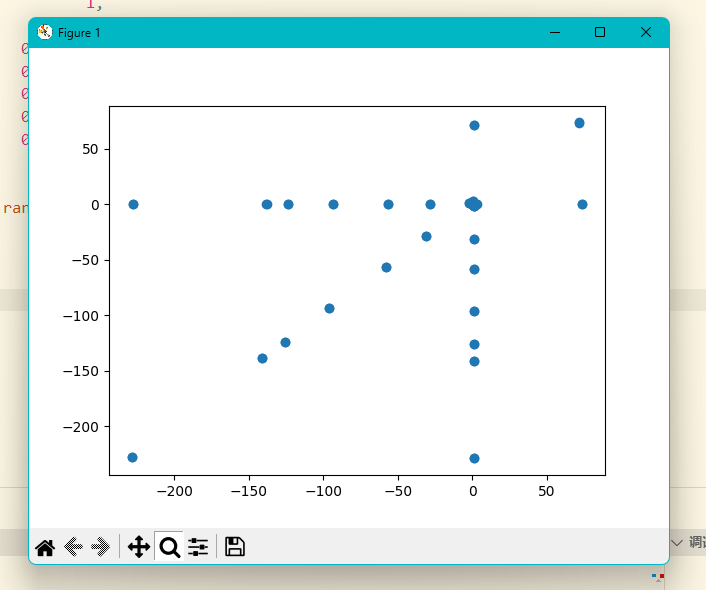
这里有一个密集位置,箭头指向应该是让我们放大看
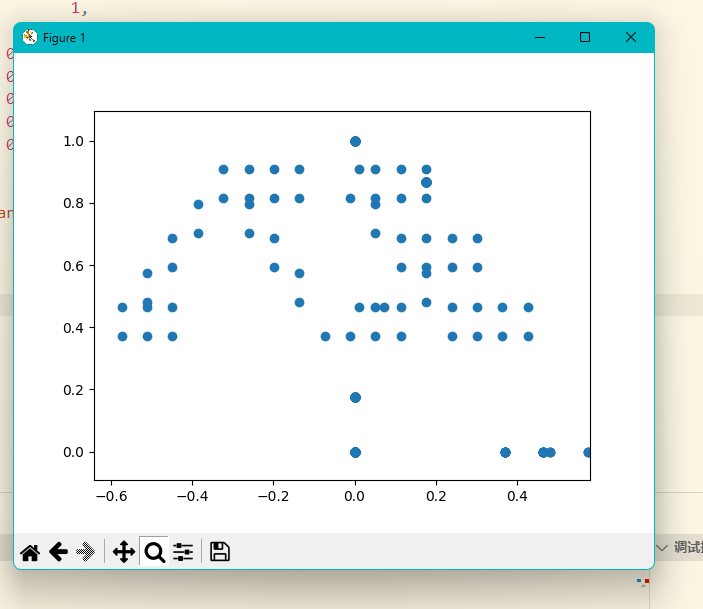
确实出现了原图的形状,但是flag旗帜的点也嵌在其中,但是对比位置好像有点问题,而且点的数量也不够,还有一个问题就是为什么这些位置没有被实际展现出来
那我们先解决为什么没有展现出来的问题,根据之前的分析,这里的几个跳转语句可能是问题所在,这里类似一个switch语句,通过数组的索引和其中的值来决定下一步的运算,有加减和一些别的运算.有点类似虚拟机的opcode
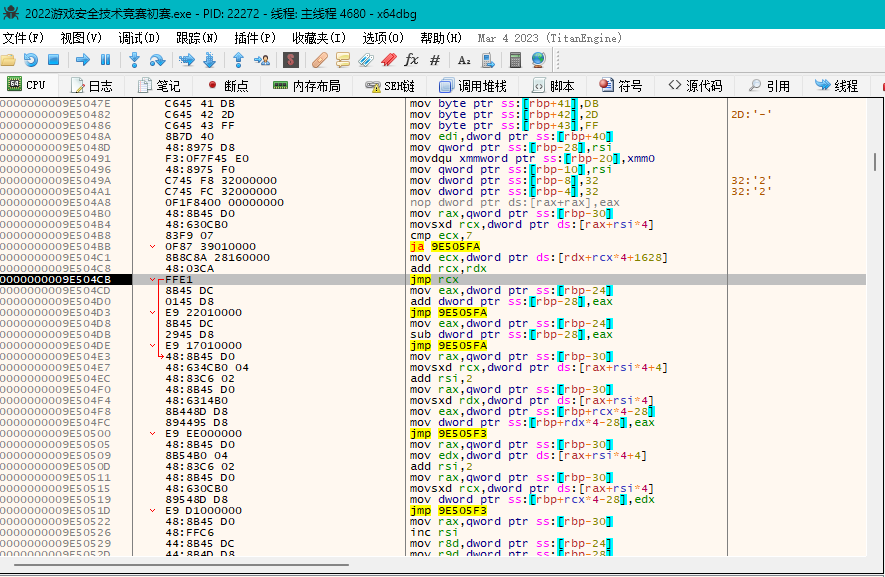
这里汇编有点没分析出来啥意思,拖到ida里调试看看伪代码
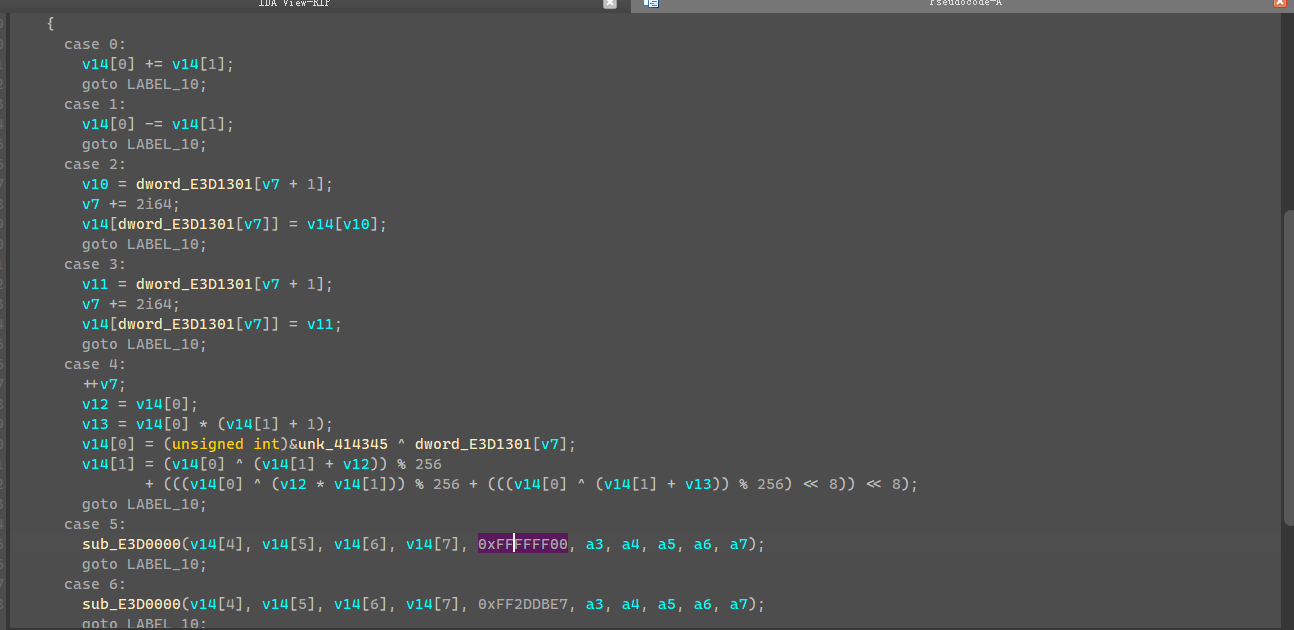
dword_E3D1301应该就是opcode数组,然后v14应该是指八个寄存器,然后case4有点没看像是一种加解密运算,然后case5和case6是两个相同的函数,传参只有一个不同,0xFFFFFF00和0xFF2DDBE7,可能与rgb的十六进制值有关,上在线转换网站上看一下
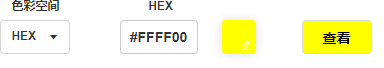
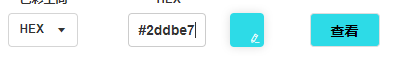
应该就是flag的黄色和原图的蓝色了,但是为什么同一个函数,只是颜色不同,怎么会有不显示和显示的情况呢,不清楚,hook一下看一下调用的时候其他参数有什么区别
hook代码:
1 | // dllmain.cpp : 定义 DLL 应用程序的入口点。 |
得到前五个参数内容
1 | a1:0xfffffc4a,a2:0x00000032,a3:0xff1fa3ac,a4:0x00130bd0,a5:0xffffff00 |
可以看到蓝色调用了31次,黄色调用了11次,正好对应正方形块数,验证了猜测.
前面的四个参数在蓝色调用的时候基本都是正数,黄色调用的时候则总会出现一些负数的情况,所以可能就是在这四个参数出了问题让绘制出现了失败,在蓝色调用的前两个参数有一些相同的情况,比如说第二个参数0x00000032这个值,出现了8次,对应了一行的八个方块,0x0000006e则对应三个方块,应该就是指的y坐标,第一个参数则可能会是x坐标,知道了这个,我们就可以通过hook这个绘制函数通过正确传参就能实现绘制,但是正确的位置在哪呢?位置被错误的计算了,只能从虚拟机运行入手了,写个脚本跑一下运行流程
1 | opcode = [0x00000002, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000004, 0x00000000, 0x00000003, 0x000003E8, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00524895, 0x00000002, 0x00000000, 0x00000003, 0x00000002, 0x00000001, 0x00000000, 0x00000002, 0x00000003, 0x00000001, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000005, 0x00000000, 0x00000003, 0x000001F4, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x005A8E2C, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000004, 0x00000000, 0x00000003, 0x000003E8, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00985AD2, 0x00000002, 0x00000000, 0x00000003, 0x00000002, 0x00000001, 0x00000000, 0x00000002, 0x00000003, 0x00000001, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00A9685D, 0x00000002, 0x00000000, 0x00000003, 0x00000002, 0x00000001, 0x00000000, 0x00000002, 0x00000003, 0x00000001, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000004, 0x00000000, 0x00000003, 0x000003E8, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000005, 0x00000000, 0x00000003, 0x000001F4, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00785CEF, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x0000012C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00963EA7, 0x00000002, 0x00000000, 0x00000003, 0x00000002, 0x00000001, 0x00000000, 0x00000002, 0x00000003, 0x00000001, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000004, 0x00000000, 0x00000003, 0x000003E8, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000005, 0x00000000, 0x00000003, 0x000001F4, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00465215, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000005, 0x00000000, 0x00000003, 0x000001F4, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00856DCE, 0x00000002, 0x00000000, 0x00000003, 0x00000002, 0x00000001, 0x00000000, 0x00000002, 0x00000003, 0x00000001, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000004, 0x00000000, 0x00000003, 0x000003E8, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00758C6E, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000005, 0x00000000, 0x00000003, 0x000001F4, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x0098A6B4, 0x00000002, 0x00000000, 0x00000003, 0x00000002, 0x00000001, 0x00000000, 0x00000002, 0x00000003, 0x00000001, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000004, 0x00000000, 0x00000003, 0x000003E8, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00856ECE, 0x00000002, 0x00000000, 0x00000003, 0x00000002, 0x00000001, 0x00000000, 0x00000002, 0x00000003, 0x00000001, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000005, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x00000258, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000008, 0x00000002, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00ABFC52, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00856ECE, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x009654EA, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x008523AC, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x0086EACC, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00EA3245, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000001, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00854AEC, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00963DCE, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x0098EE44, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x0078A213, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00526339, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x0088574E, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x0012445A, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00965243, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x0000012C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00AA23E4, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x00000168, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00AA2488, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000001A4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00965224, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x0000012C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000008, 0x00000002, 0x00000008, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00263554, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00015478, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00963524, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00AEBCDF, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x0000003C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x008547AE, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x009685AA, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x0096335A, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00965234, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x0000012C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x00000078, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x007845EE, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000B4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00482526, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00326212, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x0000012C, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x00747475, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x00000168, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x002314EC, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000002, 0x00000008, 0x00000000, 0x00000003, 0x000001A4, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000004, 0x00000002, 0x00000009, 0x00000000, 0x00000003, 0x000000F0, 0x00000001, 0x00000000, 0x00000002, 0x00000000, 0x00000005, 0x00000002, 0x00000004, 0x00000000, 0x00000002, 0x00000005, 0x00000001, 0x00000004, 0x009634EA, 0x00000002, 0x00000000, 0x00000006, 0x00000002, 0x00000001, 0x00000007, 0x00000006, 0x00000007] |
运行结果部分:
1 | ===2 reg[0]=reg[8],reg[0]=0,reg[8]=50 |
基本都是在case1的时候减了一个大数,然后call的参数就出现负数,简单的加个if条件,将减的那一步选择性的跳过,如果结果为负数,那么就不执行减操作,改下程序得到的参数貌似正常了,得到的“正确“参数如下:
1 | reg[4]=50,reg[5]=50,reg[6]=10637038,reg[7]=2907850890 |
尝试hook绘制函数传入这些参数进行绘制看看结果,试了很久一直没有显示,连原图的都不显示了,最后对照了一下第三个和第四个参数发现和之前hook来的参数不同,应该是计算的时候C有溢出但是python没有,重新用C写一遍模拟虚拟机运行的脚本运行得到第三个参数和第四个参数数组
1 | int reg6[11] = { 0xf814b4,0x1bcd69,0x87a34b,0x1cf400,0x391faa,0xebe72,0x71150,0xc7371b,0x34cf2b,0xd1b52d,0xb36fdf}; |
注入测试
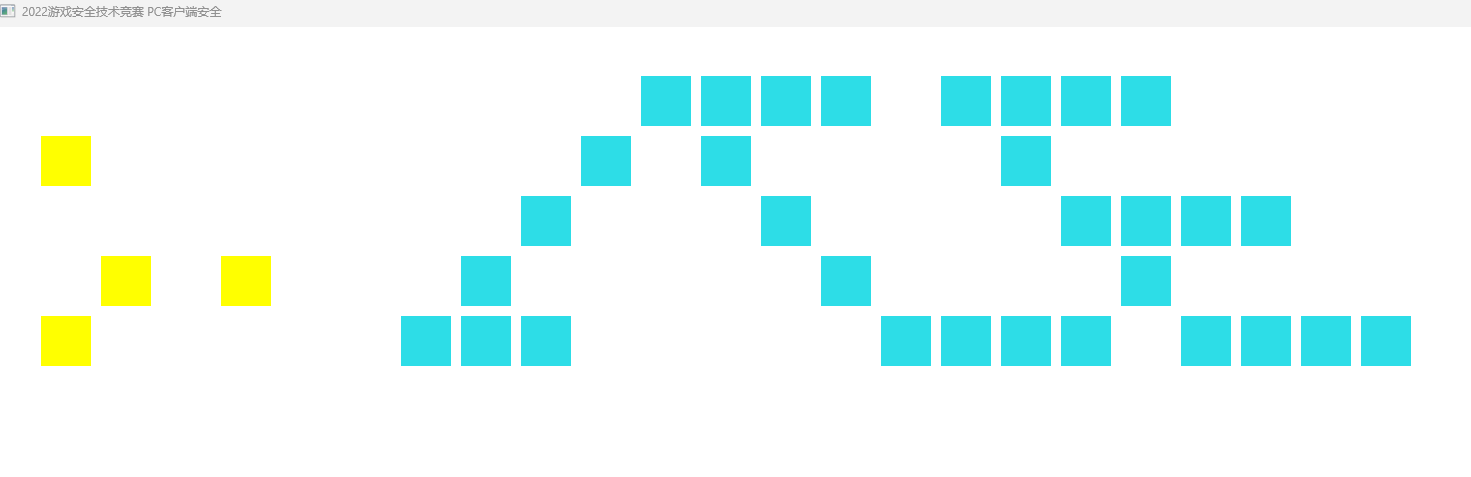
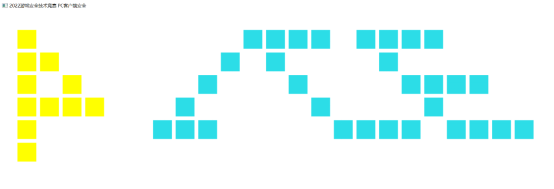
只显示了四个方块,嘶,怎么会少了7块呢,根据前两个参数的大概位置分析在第2,5,7,9次黄色函数调用处,对比一下他们的虚拟机运行情况
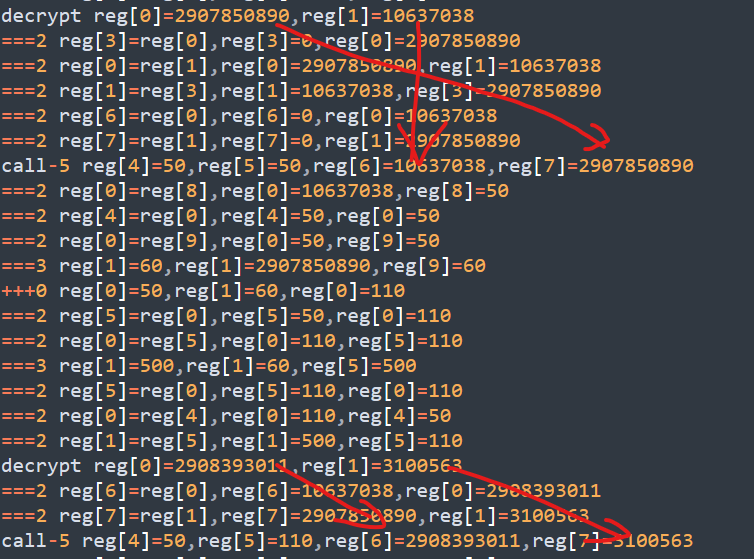
在这里看到了有些call调用的前将第三个和第四个参数分别调换了位置,刚好2,5,7,9没有调换!!!
所以根据这个再把错误的参数位置调换一下进行注入测试
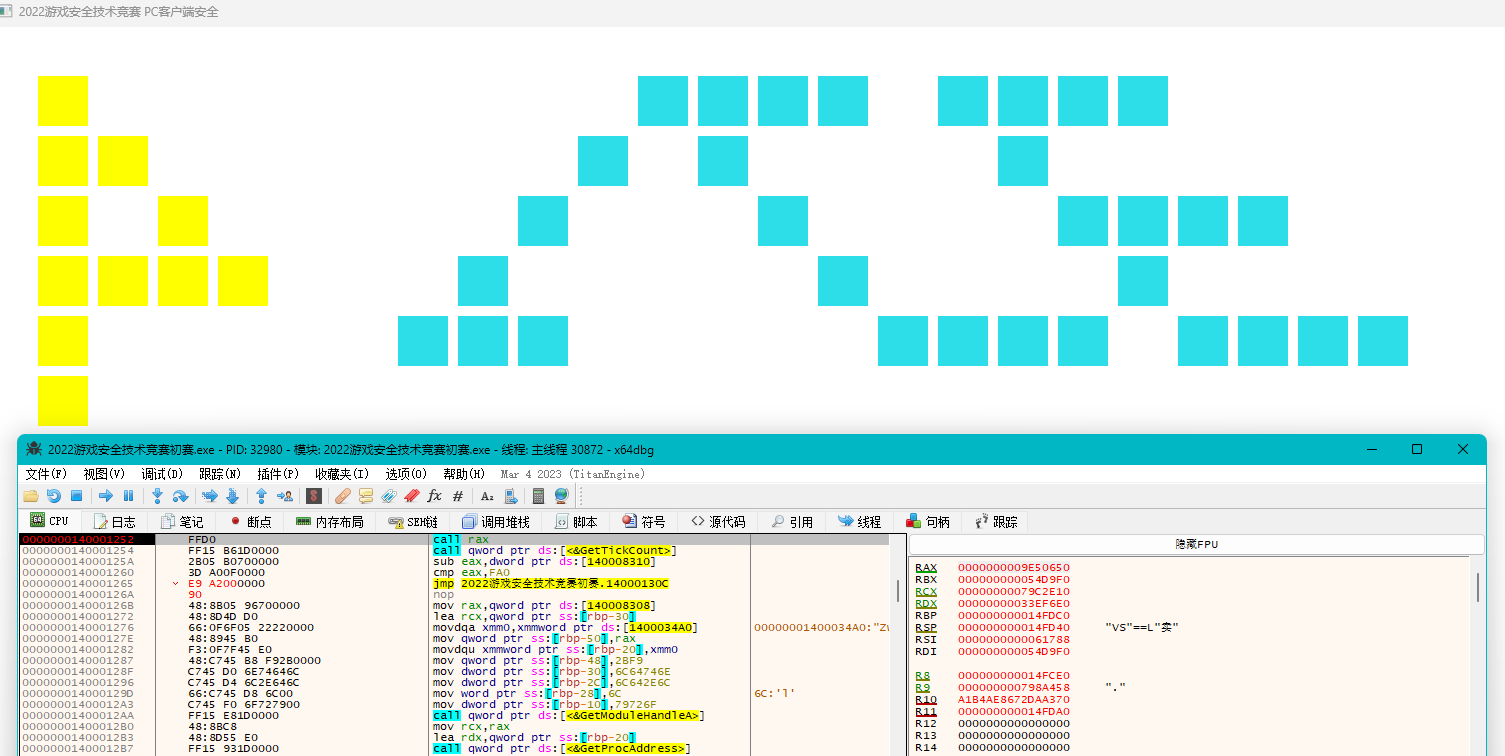
HOOK代码
1 | // dllmain.cpp : 定义 DLL 应用程序的入口点。 |